What if someone is spying on everything you do with your mobile? We have already seen that it is possible to hack an Android mobile if certain conditions are met, and in most cases there is no key clue that you can use to determine whether or not they are spying on your mobile.
If you suspect that someone may have tampered with your smartphone to spy on you, here’s how find out if your mobile is spying on you, as well as what measures you can take to avoid it.
Activa Google Play Protect

One of the first steps that spy apps use is to ask you to disable any type of protection that you have on your mobile. On Android, this is generally synonymous with Google Play Protect, the protection pre-installed on most Android phones.
Many spy apps require disabling Play Protect
The reason is simple: Google Play Protect detects many of these applications as malicious, so you prevent them from working and in some cases you can uninstall them yourself. If you suspect that your mobile may have been tampered with, it never hurts to check that Google Play Protect is activated.
To do this, open the Google Play side menu and choose Play Protect. If it is deactivated, a red icon alerting you. Tap on it and dial Search device security threats para activar Google Play Protect.
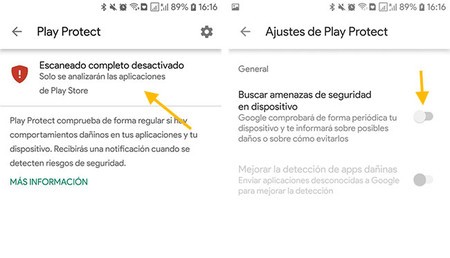
If Play Protect was disabled, it is best to go back to the previous screen and force a scan of installed apps, to detect a possible spy application. To do this, tap on the resume scan button.

Then two things can happen: that Play Protect says that everything is correct, or that it detects the harmful application and ask you to uninstall it. If this is your case, read on to see what other measures you can take.
Check installed applications
We are talking here about “walking around the house” espionage, and that generally happens through surveillance techniques. phishing in order to trick the user into installing a malicious app, or when the spy has physical access to the terminal to do the installation. For example, your boyfriend or girlfriend in an oversight.
In most cases we are not dealing with a hacker typing commands at full speed in a terminal until exclaiming ¡Eureka! and have access to the terminal, but something much more mundane: an app. An app that, like any other, can be located and uninstalled. But it takes a good eye.
Don’t be fooled by generic names like “System Service”, “Play Tools” or “Sys Tools”
The developers of these types of applications know that if the application were called Total Spy Monitor O Hacking Control Panel the user could discover them inadvertently, so that camouflage their names and icons so they look like boring system icons, like “Sync Services” or “System Service”. Your job is to look closely to find apps that are not what they seem.
In the Android settings, go to the section Applications and wait for it to finish loading the list. The way this list works may change from one Android layer to another, but the most important thing is that system apps are not displayed (which is, on the other hand, the standard behavior).
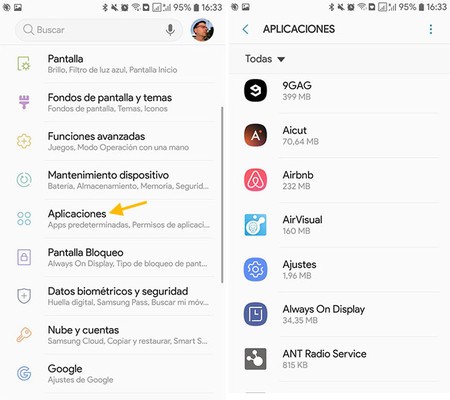
Now comes the tricky part: reviewing the list. I recommend that you go one by one, checking that you know all the applications on the list and that you have installed them on your own initiative. Spy apps generally hide in boring and generic names, and they usually stay in English.
Now, the list also shows system apps that have been updated, so the review may have its thing. When in doubt, tap on an app to see its information. System apps cannot be uninstalled (only their updates), while apps that pretend to be from the system can.
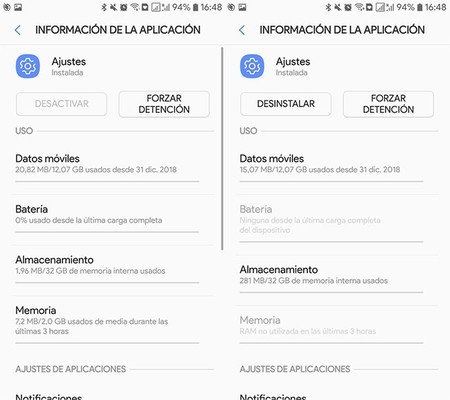 Real Settings app (left) and Settings app pretending to be real (right)
Real Settings app (left) and Settings app pretending to be real (right) Finding these phonies is as important as uninstalling any other application that appeared out of nowhere. Applications change and sometimes get redesigns or even a new name, but it never hurts to do some checking.
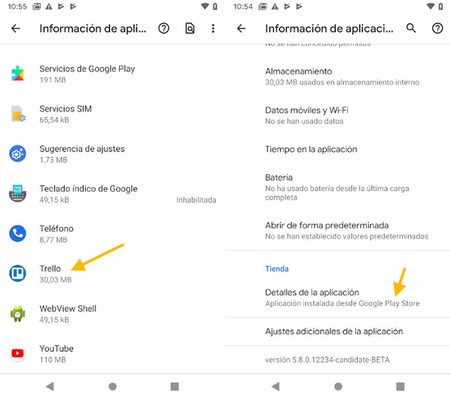
A good way to know if an app is who it claims to be is to look at where it has been installed from
One simple thing you can check is from where an application has been installed, if it has been from Google Play or from its APK. Since spying apps are not allowed on Google Play, they will generally be installed from outside of the store. To view it, tap on its name in the app list and search Details of the application, in the information.
Generally, this method will help you uncover most of the spy applications that we talked about in our article. You need to pay attention to distinguish what is normal from what is not, but it is not particularly complicated.
Check the apps that use the most battery
Spying on the user all day is hard work that drains your battery, especially those apps that take photos or videos of the user or record their position using GPS. Although they surely have their own mechanisms to minimize their impact and it is not very obvious, it is an indication that it can tell you that something is wrong.
To do this, go to the settings and enter Battery usage. The location of this menu changes a lot from one mobile to another, so I recommend that you use the search engine. In pure Android, for example, it is a context menu within the Battery section.
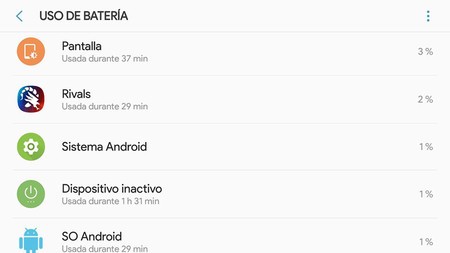
Here once again you must use the critical eye to find what is out of the ordinary. Be aware that malicious apps frequently disguise their name and icon, so just because it says “Android System”, don’t just believe it. Tap on the app to see if it is who it claims to be. You will know because system apps cannot be uninstalled.
And let’s not forget the data
In addition to wasting your battery, spying on what you’re constantly doing also requires considerable data usage, especially if it is taking photos with the mobile camera without your permission or receiving the files that you have in the gallery.
To check, go to Android settings and enter Use of data, usually hidden within the section of Connections and network. Check the apps that use the most data in search of a suspect that you do not know.
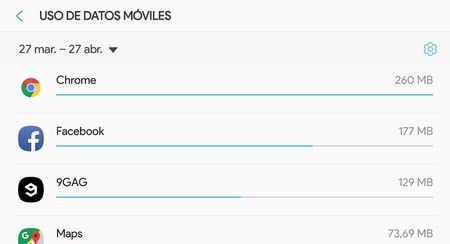
If the spy app is smart enough, it will probably wait until it has a Wi-Fi connection to synchronize the data and thus not arouse suspicion. While some mobiles allow you to see the data usage including Wi-Fi connections, in others there is no option.
Suspicious messages
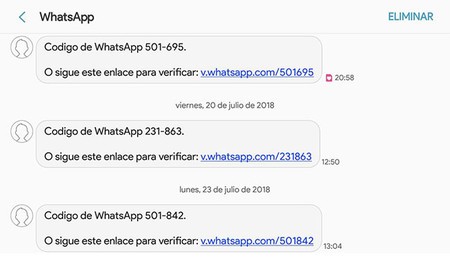
If you receive messages by SMS or mail about verification codes or new password requests, is a good reason to be suspicious. It is possible that someone has your credentials to access some services, but the system “chive” sending you an email or asking you to enter a verification code.
Most services notify you if someone tries to log in with your account
Most important accounts such as Google, Facebook or Twitter notify you by email when there is a suspicious login attempt. Although it could be that it is someone clueless who has misspelled their phone number, email or account, it is also possible that it is someone trying to impersonate your identity, especially if it happens frequently.
What to do if they are spying on your mobile

Okay, you found out that they are spying on your cell phone, now what? First of all, remember that spying on a mobile is illegal, and therefore you can file a complaint before the police. If this is what you plan to do, it is best to turn off your mobile as such and take it to the police station as a “test”.
Safe mode is your best ally
If you prefer to do without paperwork or suspect that the spy may be thousands of miles from you and the report is not going to be of much use, the best thing is that secure the ground before continuing to use your mobile.
First of all restart the mobile in safe mode. This disables all third-party applications and will almost certainly prevent spying from going further. The exception would be if the tool has obtained root access and modified the system from within, although this is not common. You can check if your mobile is rooted with apps like Root Checker.
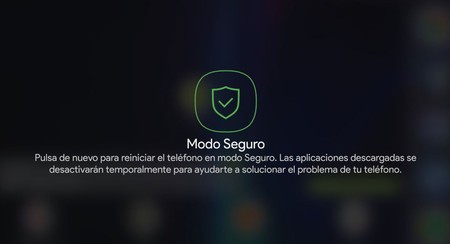 Safe mode prevents third-party apps from loading, including spyware
Safe mode prevents third-party apps from loading, including spyware The idea is to use safe mode to avoid being spied on and to be able to uninstall the apps involved. If you’re not sure, you can always factory reset your phone to make sure no trace remains.
Then it’s time to change passwords of all the accounts you have configured on your mobile. The most important is the Google account, but there could also be Facebook, Skype, LinkedIn, Twitter and more. Especially important are the credentials of banking applications and apps like Paypal.
To avoid similar situations in the future, it is best to turn on 2-step verification in all the services that you can, and if possible not by SMS code, but with specific applications or by means of notices. This way, even if someone gets your password, they won’t be able to log into your accounts without your knowledge.

When you have everything under control, it is a good time to think how the spyware got to your mobile, to prevent it from happening again. Basically two possibilities are considered: that someone who had physical access to the mobile for a few minutes did it, or that you accidentally did it yourself, believing that you installed something else. This second is somewhat more unlikely, as you should have manually granted several permissions for it to work.