Google has a security team in charge of keeping the Google Play Store clean, but sometimes some type of code appears that gives more headaches to the account. This is the case of ‘Joker ‘, a malware that has been circulating on Android for some time and that it does not stop changing its code to continue hiding from Google Play Protect searches.
‘Joker’, also known for his original man, ‘Bread,’ reappeared in January when Google removed 24 more apps, though his record on the Google Play Play is up to three years old. Now again it reappears and has been hunted with more changes on board. Joker is now able to download and install files on the phone.
‘Joker’ evolves to continue eluding Google police
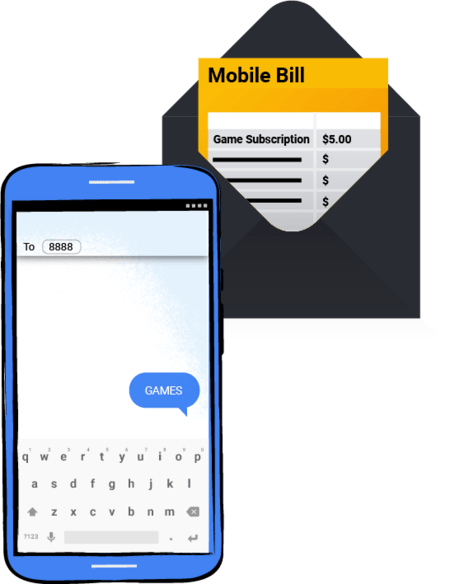
In its origins, ‘Joker’ was financed by subscribing to premium SMS services that, if not detected in time, inflated our telephone bills in a worrying way. Back in January, the malware had changed thanks to various changes to its code and WAP billing was mainly used. A method of payment for operators already in disuse but still active, and that was used by ‘Joker’ to continue spending our money.
‘Joker’ continues to be modified from time to time to bypass Google Play Protect security controls and hide inside apparently legitimate apps, but at Check Point Research They have located it again, publishing their results in a public report that can be consulted here.
The new updated version of ‘Joker’ is capable of downloading additional malware on our Android phones and tablets, a malware that in turn subscribes to premium services, costing users who are affected. In the latest detection, Check Point Research has located up to 11 different package names in different applications that Google has already removed from the Play Store.
“Joker, one of the most prominent types of malware on Android, continues to find its way into the official Google app market as a result of small changes to its code, allowing it to overcome Play Store security and verification barriers. […] This time, however, the evil actor behind Joker adopted an ancient technique from the conventional PC threat landscape and used it in the world of mobile applications to avoid detection by Google, “says Check Point Research in his report.
Apparently, the new ‘Joker’ code, very similar to the one previously detected, would have used a technique widely used in Windows, the one to hide the fingerprint of your code hiding the DEX file during the moment of the mark. Be that as it may, ‘Joker’ has been detected again and the apps related to this new iteration of its code have been removed. But knowing his record so far, it is certain that we will see him again in the coming months.
Track | BGR