Misconfiguration of real-time cloud services in some applications has been found to allow access to sensitive user data; such as email addresses, private messages, photos and even passwords. This wrong configuration was applied in certain Android apps that accumulate more than one hundred million downloads.
For an app to offer services to users, it needs to store certain information in a database in order to constantly contrast it and download what the person needs. For example, a taxi app requires storing a username, address, or payment methods; managing all this sensitive information through databases in real time so that the user does not suffer delays in the applications. The problem, as CheckPoint Research found, is that not all apps secure these vital databases.
Real-time databases without any protection system
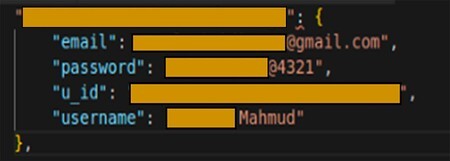 Information obtained from an unprotected database. CheckPoint Image
Information obtained from an unprotected database. CheckPoint Image We have to say that the serious privacy error affects a small number of applications; without escaping applications with more than ten million downloads, such as Logo Creator or AstroGuru. According to researchers from the security agency CheckPoint, an attacker can access sensitive information just by making a request to the database of these apps.

Since applications need to store information in databases, and these apps require constant access to stored information, developers use real-time databases to streamline processes without losing apps appeal to users. The problem comes when access to these databases is not protected: with intercepting requests, analyzing URLs and make an external request masking the web extremely sensitive information is possible. This is a serious privacy and security problem.
As specified by CheckPoint, the Researchers were able to obtain email addresses, usernames, passwords, photographs and even chat messages which were supposed to be private. All stored in real-time databases that did not prevent a request from outside the applications.
Since real-time databases are not protected by authentication, any stored information is vulnerable to those who make requests from outside the affected apps.
Apps like Logo Maker, AstroGuru, Screen Recorder, iFax or T’Leva proved vulnerable to unauthorized requests: If you have any of these apps installed, it is best to uninstall them. CheckPoint communicated its discovery to the developers and also to Google. Several of the apps were updated following the CheckPoint Research advisory and are currently not vulnerable.
More information | CheckPoint